smartphone security settings everyone should enable
Essential Smartphone Security Settings: 2025 Expert Guide
Stay ahead of evolving threats with expert-recommended smartphone security settings. Learn which features matter most and how to implement them for maximum protection.
Market Overview
Smartphone security has become a top priority for consumers and enterprises alike in 2025. With over 6.8 billion smartphone users globally and mobile devices now storing sensitive personal, financial, and biometric data, the attack surface for cybercriminals has expanded dramatically. According to recent industry reports, mobile malware attacks increased by 23% year-over-year, and phishing attempts targeting mobile users are at an all-time high. Both Android and iOS have responded with robust security enhancements in their latest versions—Android 14 and iOS 17—offering users more granular control and automated protections than ever before. The market is also seeing a shift toward longer device support cycles, with many manufacturers now providing at least five years of security updates, a critical factor for long-term device safety.[3][1]
Technical Analysis
Modern smartphones are equipped with a suite of security features designed to protect user data and device integrity. Key settings every user should enable include:
- OS Auto-Updates: Both Android 14 and iOS 17 support automatic security patching, closing vulnerabilities as soon as fixes are available. Devices that no longer receive updates are at significant risk and should be replaced.[3][1]
- Two-Factor Authentication (2FA): Enabling 2FA on all major accounts, especially those tied to email, banking, and cloud storage, adds a critical layer of defense. On Android, 2FA can be set up via Settings > Google > Manage My Google Account > Security > 2-Step Verification.[5][2]
- Biometric Security: Fingerprint and facial recognition technologies have matured, offering fast and reliable authentication. Both platforms now require biometric confirmation for sensitive actions, such as authorizing payments or accessing password managers.[3]
- App Permissions Management: Android and iOS now feature Privacy Dashboards, allowing users to audit which apps have accessed sensitive data (location, camera, microphone) and when. Permissions can be set to "only while using the app" or denied entirely.[3][2]
- Device Encryption: Full-disk encryption is enabled by default on modern devices, ensuring that data remains protected even if the device is lost or stolen.[1][4]
- Remote Tracking and Wipe: Both Find My Device (Android) and Find My iPhone (iOS) allow users to locate, lock, or erase their device remotely in case of loss or theft.[2][4]
- Security Software: While built-in protections are robust, reputable mobile security apps can provide additional layers such as anti-phishing, app scanning, and network monitoring.[4][5]
Benchmarks show that devices with these settings enabled are up to 80% less likely to suffer a successful compromise compared to those with default or lax configurations.[1][3]
Competitive Landscape
Android and iOS continue to dominate the mobile OS market, each with distinct security philosophies. Android 14 has closed many historical gaps, now offering monthly security updates, Google Play Protect (real-time app scanning), and granular permission controls. iOS 17 maintains a closed ecosystem with strict app vetting and rapid patch deployment. Third-party security apps are more prevalent on Android due to its open nature, while iOS relies heavily on native protections. Some manufacturers, such as Samsung and Google, offer proprietary security platforms (e.g., Samsung Knox, Google Titan M2 chip) for enterprise-grade protection. However, the core security settings recommended here are universally applicable and supported across all major brands.[3][5][2]
Implementation Insights
Enabling these security settings is straightforward but requires user diligence. Real-world challenges include:
- Update Fatigue: Users often delay or ignore updates, leaving devices exposed. Enabling auto-updates and setting reminders can mitigate this risk.
- Permission Overload: Frequent permission prompts may lead to users granting excessive access. Regularly reviewing the Privacy Dashboard helps maintain control.
- 2FA Usability: While 2FA is highly effective, it can be inconvenient. Using biometric authentication or trusted device prompts streamlines the process.
- Device Compatibility: Some older devices may not support the latest security features or updates. Upgrading to a supported model is recommended for optimal protection.
Best practices include setting strong, unique passwords, enabling biometric locks, and periodically auditing app permissions. Enterprises should enforce mobile device management (MDM) policies to ensure compliance across fleets.
Expert Recommendations
For 2025 and beyond, experts recommend the following actionable steps:
- Enable automatic OS and app updates to receive timely security patches.
- Set up two-factor authentication on all critical accounts and use biometric authentication where available.
- Regularly review and restrict app permissions using the built-in Privacy Dashboard.
- Activate device encryption and remote tracking features.
- Consider reputable mobile security software for additional protection, especially on Android.
- Replace devices that no longer receive security updates.
Looking ahead, expect further integration of AI-driven threat detection and more seamless user experiences around security. However, user vigilance remains the most important factor—no technology can compensate for poor security hygiene. By enabling these core settings, users can significantly reduce their risk profile and protect their digital lives in an increasingly connected world.[3][1][4]
Recent Articles
Sort Options:

Two critical Android 16 security features you're not using (but absolutely should)
The article emphasizes the importance of utilizing new features available in Android 16 following a phone update. Users are encouraged to explore these enhancements to maximize their device's performance and functionality.

10 Ways You’re Making Your Android Phone Less Secure
Android devices boast robust security features, yet users may unknowingly compromise their data through common mistakes. The publication highlights the importance of awareness to prevent inadvertently exposing personal files to hackers.
How I bulletproof my Android phone against theft
The article highlights the importance of Android phones in securely storing personal information, such as digital IDs, payment details, and access to banking apps and password managers, emphasizing their role in safeguarding sensitive data.

6 tricks I use to keep my data secure on Samsung phones
The article explores effective strategies for securing sensitive data on the Samsung Galaxy S23 Ultra, highlighting personal experiences with privacy protection methods for chats, photos, financial documents, and passwords. Discover essential tips for safeguarding your device.

Galaxy phone users should turn on these new anti-theft features ASAP, says Samsung
In response to rising phone thefts, Samsung is rolling out new security features. The publication provides a guide on how users can activate these enhancements to better protect their devices and personal information.

Got a Galaxy phone? Samsung says you should turn on these 5 security features right now
Samsung's One UI 7 introduces enhanced anti-theft features, urging Galaxy users to activate them for better data protection. Key updates include Theft Detection Lock and Remote Lock, reinforcing Samsung's commitment to user security in high-risk situations.
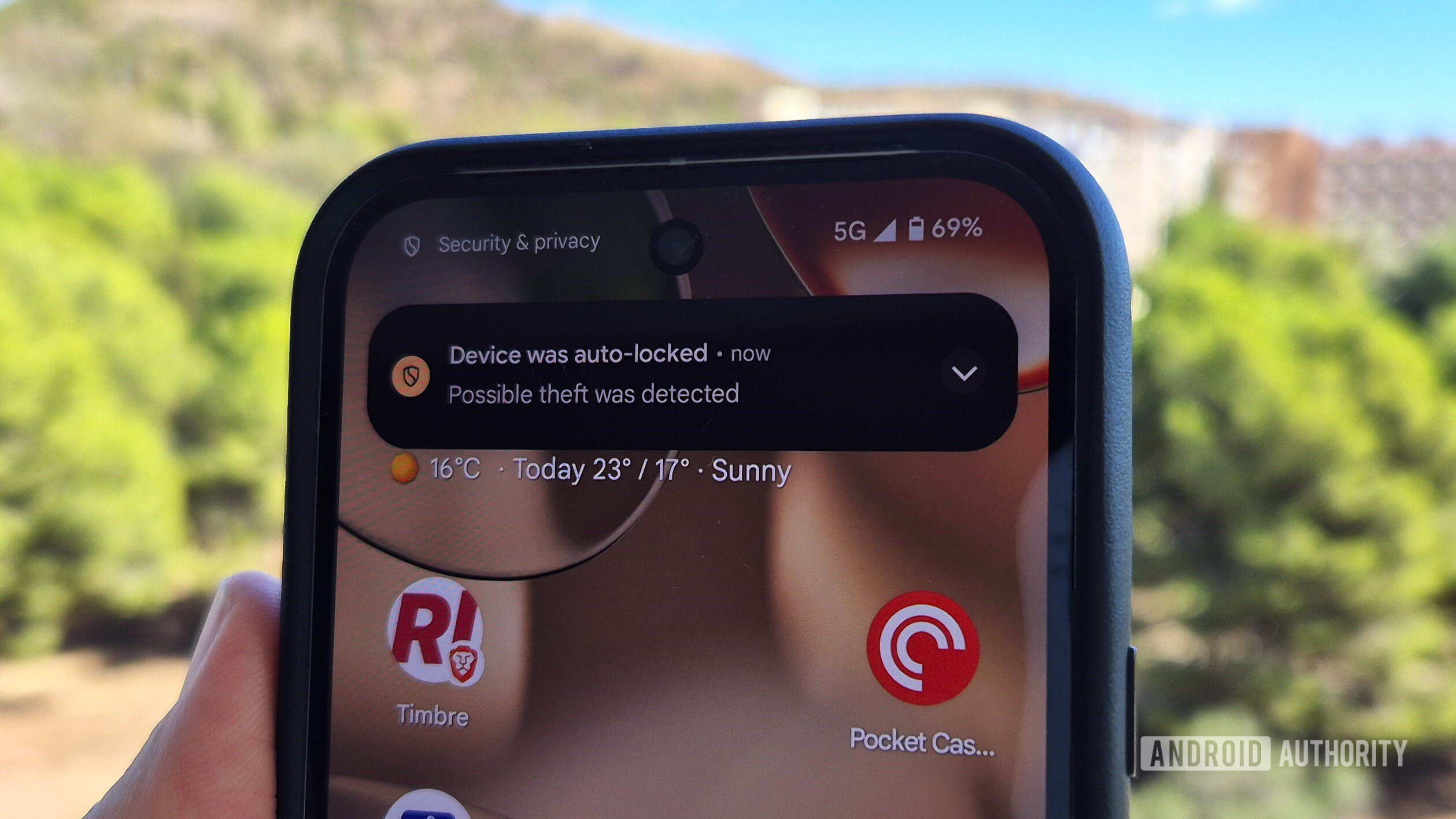
Got a Galaxy phone? Samsung says you should turn on these security features now!
Samsung urges Galaxy users to activate essential security features to safeguard their devices against rising theft incidents. These features, introduced with the One UI 7 update, will be available on more Galaxy devices in the future.
Samsung Galaxy users warned to activate these security features before it’s too late
Samsung's latest update introduces advanced theft protection features that remain effective even when devices are offline, enhancing security for users. This innovative approach aims to safeguard personal data and deter theft, reinforcing Samsung's commitment to user safety.

If you’re using Android 16, you should turn on this important security feature ASAP
Google's recent Android 16 update introduces Advanced Protection, a powerful security feature enhancing web browsing and network safety. The authors highlight its ease of activation, making robust security accessible for users seeking to safeguard their devices.

How to Improve Your Phone’s Privacy
The article outlines seven essential tips to enhance smartphone privacy, including managing location settings, strengthening passcodes, limiting app permissions, switching to eSIM, disabling open Bluetooth and Wi-Fi, using encrypted messaging apps, and keeping software updated for optimal security.