No banking apps on your custom ROM? This new initiative could help.
A new European initiative, UnifiedAttestation, aims to create an open-source alternative to Google’s Play Integrity checks, enhancing security for banking and financial apps on custom ROMs. Supported by Volla and Murena, this project addresses significant compatibility issues.
10 March 2026
Citi Braces for Busy Spell for Financial Sponsors Deals in Asia
Citigroup Inc. is enhancing its investment banking division focused on financial sponsors, responding to a surge in deal activity as firms aim to deploy capital effectively. This strategic move positions Citigroup to capitalize on growing market opportunities.
10 March 2026
I’m already worried about the Google Pixel 11 Pro Fold
The Pixel 11 Pro Fold is poised to be a pivotal release for Google, especially after the lackluster performance of its predecessor. Recent leaks suggest it may not meet expectations, raising concerns about its innovative potential.
10 March 2026
AT&T states why it's important to stay connected before, during and after an accident
The article emphasizes the critical role of timing in various contexts, highlighting how strategic timing can significantly impact outcomes. The authors explore examples that illustrate the importance of seizing the right moment for success.
10 March 2026
Nvidia Is Reportedly Developing Its Own Answer to OpenClaw
Nvidia is entering the growing market of agentic AI assistant platforms, showcasing its commitment to innovation in artificial intelligence. This move highlights the company's strategy to leverage AI technology for enhanced user experiences and competitive advantage.
10 March 2026
You Could Be Next
The article explores the precarious reality of workers in the AI training data industry, highlighting their struggles with low pay, job instability, and intense surveillance. As automation advances, many find themselves training the very systems that threaten their careers.
10 March 2026
GreedFall: The Dying World sets sail with confidence before sinking beneath an ocean of bad ideas and even poorer execution
GreedFall: The Dying World struggles under the weight of its predecessor's lore, lacking a compelling narrative and failing to evolve into a more engaging RPG experience. The publication critiques its inability to innovate within the genre.
10 March 2026
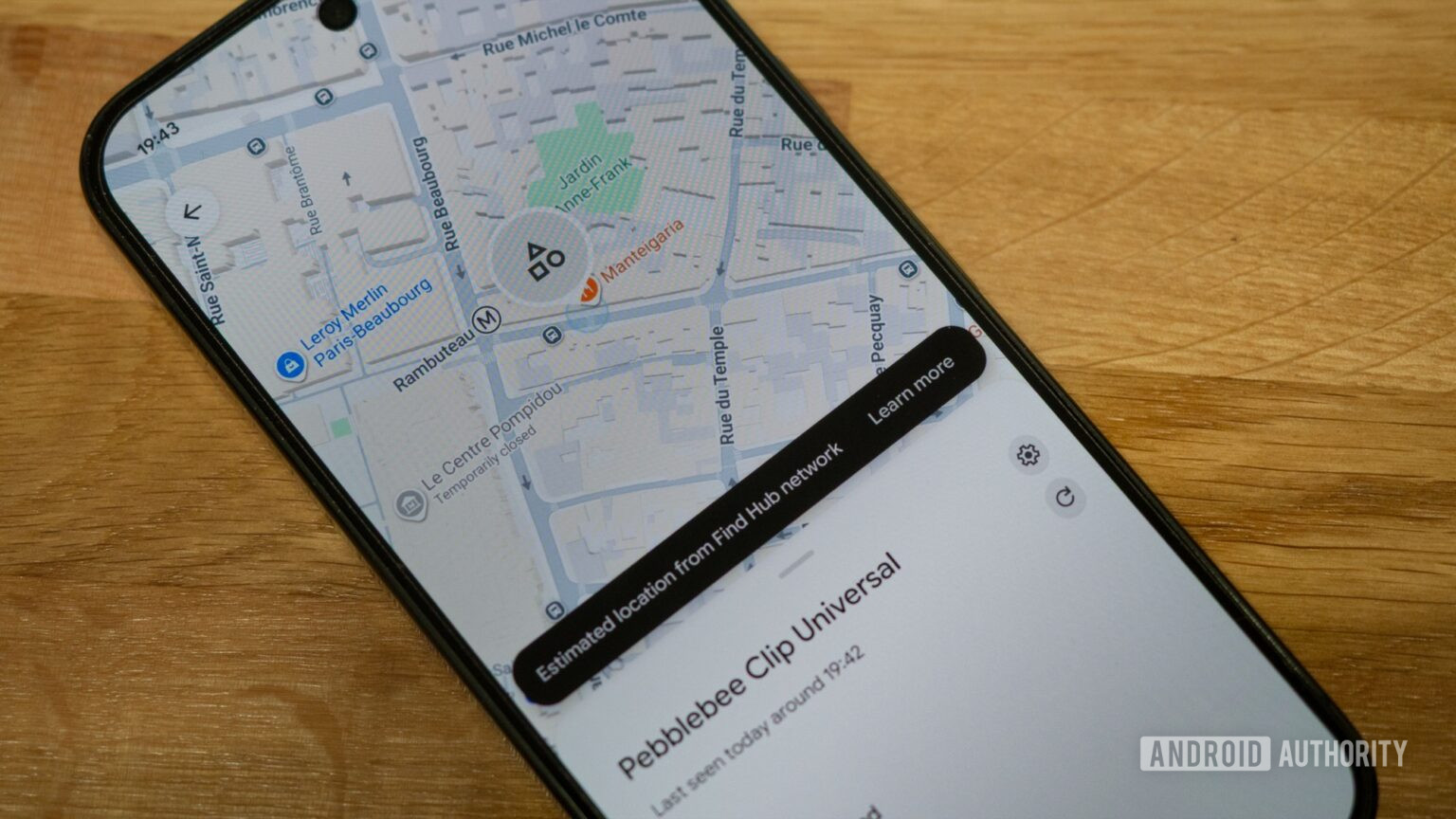
Google Find Hub update makes tracking your lost device quicker at the cost of security
Google has streamlined access to its Find Hub app by removing the biometric requirement, allowing quicker access to Devices and People lists. Users may still encounter verification prompts after inactivity or signing out, enhancing flexibility in security options.
10 March 2026
US Bitcoin ETFs add $167M as altcoin funds extend outflows
US Bitcoin ETFs experienced a significant boost with $167 million in inflows on Monday. In contrast, Ether, XRP, and Solana funds faced three-day outflows, highlighting the mixed trends within the recovering crypto market.
10 March 2026
The Oppo Find N6 could share a crucial feature with the iPhone Fold
The article explores the potential for the iPhone Fold and Oppo Find N6 to utilize similar crease technology, highlighting advancements in foldable smartphone design. This comparison could reshape consumer expectations in the evolving mobile device market.
10 March 2026
Applogika Achieves AWS Cloud Operations Services Competency, Expanding Enterprise Cloud Governance Capabilities
Applogika has achieved the AWS Cloud Operations Services Competency, showcasing its expertise in cloud governance and observability. This recognition highlights the firm's ability to enhance enterprise cloud environments, ensuring operational excellence and compliance across AWS infrastructures.
10 March 2026
Australia: NSW planners approve 400MWh Burroway solar-plus-storage despite community objections
The NSW Independent Planning Commission has greenlit Edify Energy's innovative 400MWh Burroway solar-plus-storage project, marking a significant step forward in Australia's renewable energy landscape and enhancing the country's commitment to sustainable energy solutions.
10 March 2026
Secure Your Spot at RSAC 2026 Conference
Summary Not Available
23 March 2026
[Dark Reading Virtual Event] Shields Up: Key Technologies Reshaping Cybersecurity Defenses
Summary Not Available
19 March 2026
RPCS3 Emulator boasts over 1500 FPS on the Minecraft title screen — platform hails performance landmark, one frame rendered every 0.00064 seconds
The RPCS3 emulator team highlights significant optimizations, yet fans express frustration over the continued unplayability of many titles without advanced hardware. This ongoing debate underscores the challenges of retro gaming and emulator performance.
10 March 2026
This stylish Meta Ray-Ban rival just put Gemini and ChatGPT on your face
Rokid's latest update for its smart glasses introduces Google Gemini alongside ChatGPT, enabling users to seamlessly switch between four AI models. This advancement positions Rokid as a stylish competitor to Meta's Ray-Ban smart glasses.
10 March 2026
iOS 26.4 adds a new setting to further tone down the Liquid Glass shimmer
Apple's iOS 26.4 introduces a new setting to minimize the bright flashes of the Liquid Glass interface, enhancing user experience. This update aims to provide a more subtle interaction with buttons and the keyboard, addressing mixed feedback from users.
10 March 2026
The Best Microcurrent Devices for Firmer Skin in 2026
After extensive testing of microcurrent devices over two months, the publication highlights the top performers that demonstrated significant results, offering insights for those interested in effective skincare technology. Discover which devices made the cut for optimal outcomes.
10 March 2026
Why IDPs are the Only Way to Scale Kubernetes Beyond Experts
Kubernetes serves as the default control plane but presents complexities for developers. Internal developer platforms (IDPs) are emerging to simplify operations, enhance scalability, and streamline onboarding, allowing developers to concentrate on coding rather than infrastructure management.
10 March 2026
Forget the Amazon Spring Sale: the HP printer sale at Argos has some unbelievable deals right now from £28
A special promotion offers 20% off select printers with the code HP20. This limited-time deal provides an excellent opportunity for customers to upgrade their printing solutions while enjoying significant savings. Don't miss out on this fantastic offer!
10 March 2026
Oracle’s Biggest Earnings Challenge Is a Market Fixated on Risk
Oracle Corp faces significant investor skepticism regarding artificial intelligence, leading to a challenging outlook ahead of its upcoming earnings report. Analysts suggest that the anticipated results may not alleviate concerns surrounding the tech giant's future in the AI landscape.
10 March 2026











![[Dark Reading Virtual Event] Shields Up: Key Technologies Reshaping Cybersecurity Defenses](https://eu-images.contentstack.com/v3/assets/blt6d90778a997de1cd/bltec9f14c11f342d6f/69161ac9bc68b50a22001b58/DRVE_Event_20251203.jpg?width=1280&auto=webp&quality=80&disable=upscale)